01.What is zero trust?
Zero Trust is a modern security model designed with the principle of "never trust, always verify." It requires that all devices and users, whether they are inside or outside the organization's network, must be authenticated, authorized, and periodically verified before being granted access.
In short, "zero trust" is "don't trust anyone until they verify it."
Zero Trust prevents security breaches by removing implicit trust from the system architecture, requiring verification at each access point rather than automatically trusting users within the network. Take a multi-layered approach to protecting modern network environments, including:
● Network segmentation
● 7-layer threat protection
● Simplified fine-grained user access control
● Comprehensive security monitoring
● Security system automation
With the rise of remote working, bring-your-own-device (BYOD) and cloud-based assets that are outside the perimeter of an enterprise-owned network, traditional perimeter security becomes inadequate. This is where zero trust comes in. Zero Trust Architecture (ZTA) is designed without traditional network boundaries and abandons the traditional security boundary model (castle moat model).
At its core, Zero Trust security not only acknowledges that threats exist both inside and outside the network, but also assumes that a breach is inevitable (or likely to have already occurred). Therefore, a zero-trust security system continuously monitors for malicious activity and limits user access to only what is needed to do the job. This effectively prevents users (including potential bad actors) from moving laterally through the network and accessing any unrestricted data.
Zero Trust security can be applied in a variety of ways, depending on your architectural design and approach.
Zero Trust Network Access (ZTNA), sometimes referred to as "software-defined perimeter," is the most common implementation of the zero trust model. ZTNA is based on micro-segmentation and network isolation, replacing the need for a VPN, allowing access to the network after verification and authentication.
According to Gartner, in the ZTNA pattern, "access is restricted to a set of named entities through a trust broker. Before allowing access, the broker verifies the identity, context, and policy compliance of the specified participants and disallows access elsewhere in the network." Lateral movement". This minimizes the attack surface and greatly reduces security risks.
Zero Trust Application Access (ZTAA) is also based on Zero Trust principles, but unlike ZTNA, it goes a step further and protects not just the network but the applications as well. ZTAA assumes that all networks have been compromised and restricts access to applications until the user and device are authenticated. This approach effectively prevents attackers from entering the network and protects connected applications.
Zero Trust Access is an overarching pattern that includes ZTAA and ZTNA to provide end-to-end Zero Trust across the entire architecture, including all networks and applications. It provides identity-based security that considers not just who is on the network, but what is on the network - extending Zero Trust to the provider itself. In this way, enterprises can obtain comprehensive data privacy protection in a true zero trust environment.
02. The history of zero trust security
John Kindervag proposed the original zero trust model in 2010. As a principal analyst at Forrester Research, Kindervag realized that traditional access models were based on outdated assumptions that enterprises should trust everything within their network. The idea was that perimeter-based security (i.e., firewalls) would be enough to authenticate user access and completely secure the network.
However, as more and more employees began to access systems remotely through various types of devices and various connections, this trust structure proved insufficient to effectively manage a distributed workforce. Kindervag was aware of this vulnerability and developed Zero Trust as a response.
At the same time, Google also began developing its own zero-trust system. Google created BeyondCorp to migrate traditional virtual private network (VPN) access policies to a new infrastructure where no system is trusted and all endpoints have access controls and monitor. Later, Google developed BeyondProd, which provides a zero-trust approach to securely managing code deployment in a cloud-first microservices environment.
Kindervag’s zero trust model and Google’s BeyondCorp both revolve around a few key principles:
● Segmentation
Traditional networks expose direct access to all data assets, servers, and applications. The Zero Trust model breaks down various subsets of these resources so that users cannot directly access them without going through a tightly controlled gateway. This is sometimes called "network isolation". Micro-segmentation technology takes this concept further by isolating workloads from each other, allowing administrators to monitor the flow of information between different servers and applications, not just between clients and servers.
● Access control
Whether users are in the office or working remotely, they can only access information and resources appropriate for their respective roles. Every part of the network should have authentication and authorization verification to ensure that traffic is coming from authenticated and authorized users, regardless of the location or origin of the request.
● Visibility
Gateways should inspect and log all traffic, and administrators should regularly monitor logs to ensure users are only trying to access systems they are allowed to access. Typically, administrators use cloud access security agent software to monitor traffic between users and cloud applications and issue warnings if suspicious behavior is detected.
● With a zero-trust model, enterprises can eliminate direct access to networks and resources, establish fine-grained access controls, and gain visibility into user behavior and traffic. However, they need models to guide implementation.
Google has set the industry standard for Zero Trust by providing extensive documentation for businesses looking to emulate BeyondCorp. However, most companies found that Google's approach was interesting in theory but unworkable in practice (its implementation would essentially require stripping and replacing Google's existing network components and global architecture). Instead, enterprises must rely on a combination of third-party services to implement a zero-trust architecture within their infrastructure.
03.Basics of the zero trust model
Zero Trust is an integrated, end-to-end security strategy based on three core principles:
● Never trust, always verify
Authentication and authorization are always based on all available data points, including user identity, location, device, data source, service, or workload. Continuous authentication means that there are no trusted zones, devices or users.
● Assume there is a vulnerability
By assuming defenses have been penetrated, a stronger security posture can be adopted to address potential threats, minimizing the impact if a breach occurs. Limit the “blast radius”—the range and scope of potential damage caused by a breach—by segmenting access and reducing the attack surface, verifying end-to-end encryption, and monitoring the network in real time.
● Apply minimum privilege access
Zero Trust follows the Principle of Least Privilege (PoLP), which restricts access to any entity to only the least privileges necessary to perform its functions. In other words, PoLP prevents users, accounts, computing processes, etc. from having unnecessarily broad access across the entire network.
The above principles lay the foundation for building a Zero Trust Architecture (ZTA).
Additionally, the eight pillars of Zero Trust security form a defensive architecture designed to meet the needs of today’s complex networks. These pillars represent key areas of focus for classifying and implementing a Zero Trust environment, respectively.
● Identity security
An identity is an attribute or set of properties that uniquely describes a user or entity. Often referred to as user security, it centers on using authentication and access control policies to identify and authenticate users trying to connect to a network. Identity security relies on dynamic and contextual data analysis to ensure the right users are allowed access at the right time. Role-based access control (RBAC) and attribute-based access control (ABAC) will be applied to the policy to authorize users.
● Endpoint security
Similar to identity security, endpoint (or device) security performs "system of record" verification on devices attempting to connect to the corporate network, including user-controlled and autonomous devices such as IoT devices. It focuses on monitoring and maintaining equipment health at every step. Organizations should inventory and secure all agent devices, including mobile phones, laptops, servers and IoT devices, to prevent unauthorized devices from accessing the network.
● Application security
Application and workload security includes on-premises and cloud-based services and systems. Securing and managing the application layer is key to successfully adopting a zero-trust posture. Security encapsulates every workload and compute container to prevent data collection and unauthorized access across the network.
● Data security
Focus on protecting and enforcing access to data. To do this, the data is classified and then isolated from everyone except the users who need access. This process includes classifying data based on mission criticality, determining where the data should be stored, and developing a data management strategy accordingly as part of a robust zero-trust approach.
● Visibility and analytics
Visibility into all security processes and communications related to access control, segmentation, encryption, and other Zero Trust components provides critical insights into user and system behavior. Monitoring the network at this level improves threat detection and analysis while enabling informed security decisions and adapting to the ever-changing security environment.
● Automation
Improve scalability, reduce human error, and increase efficiency and performance by automating manual security processes that apply policies consistently across your enterprise.
● Infrastructure security
Ensure systems and services within your workload are protected from unauthorized access and potential vulnerabilities.
● Network security
Focus on isolating sensitive resources and preventing unauthorized access. This involves implementing micro-segmentation technology, defining network access, and encrypting end-to-end traffic to control network traffic. These principles lay the foundation for building a Zero Trust Architecture (ZTA).
04. Benefits of Zero Trust
An effectively implemented zero trust model should go beyond security and enable the enterprise to operate more efficiently, providing secure, granular access to everyone, including:
● Reduce infrastructure complexity
● Work in hybrid physical and cloud environments
● Work on a variety of different devices and physical locations
● Comply with internal and regulatory standards
Virtual private networks (VPNs) often struggle to adapt to the complexities of modern technology environments. While zero trust and VPNs are not mutually exclusive, many organizations find that a VPN is not necessary after adopting a zero trust model.
VPN provides perimeter-based security that provides network-wide access; in contrast, ZTNA only allows access to specific resources after verification and authentication. ZTNA strengthens the security of internal and external networks by reducing the attack surface and implementing more granular controls compared to VPNs. In addition, ZTNA also has higher flexibility and scalability, improves resource utilization and reduces IT pressure.
05. Barriers to implementing zero trust network access
While the security benefits of Zero Trust are clear, enterprises can encounter significant obstacles when migrating to a new cybersecurity model. Even with third-party services, many enterprises still struggle to successfully implement zero-trust network access.
According to a report by Cybersecurity Insiders, only 15% of companies have developed a zero trust strategy, and another 63% intend to develop a strategy in the near future. Likewise, a survey conducted in 2019 revealed that only 16% of physical data centers had implemented a zero-trust architecture.
If your business plans to adopt a zero trust approach, you need to anticipate and plan for these potential challenges.
● Adapt to complex and mixed environments
Modern enterprises have highly complex and distributed infrastructures. The challenge for IT leaders is to create a zero trust strategy for an environment that may have hundreds of different databases, servers, agents, on-premises applications, and third-party SaaS applications. To further complicate matters, each application may run in multiple different physical and cloud data centers, each with its own network and access policies.
For many enterprises, bringing networks to a level that is Zero Trust compliant requires extensive custom configuration and time-consuming development projects, a burden that can push organizations to take shortcuts that are not scalable or insecure.
● Use a hodgepodge of tools
To build an infrastructure that supports a zero-trust model in such an organization, a number of different micro-segmentation tools, software-defined perimeter tools, and identity-aware brokers must be implemented. This range of tools may include VPNs, multi-factor authentication (MFA), device approvals, intrusion prevention systems (IPS), single sign-on (SSO) solutions, and more.
However, many of these systems are cloud provider, operating system and device specific. Instead of supporting a homogeneous set of devices, many organizations run across multiple clouds and physical data centers, with users using both Macs and Windows, servers running multiple Linux distributions or Windows Server versions, and supporting a variety of different network-connected devices. .
Vendors of these tools often require enterprises to purchase redundant technology to support all of these environments. These vendors may also add unnecessary complexity by focusing on the network layer rather than placing control close to users and applications.
● Transition from legacy systems
Traditional systems and third-party applications designed around implicit trust present additional challenges. Enterprises often cannot configure legacy or third-party applications in a zero-trust-compliant manner without rebuilding. Administrators often must create their own frameworks and infrastructure to support them, adding complexity, time and expense, and requiring support at all levels.
● Close security loopholes
Transitioning to zero trust may introduce security vulnerabilities, thereby increasing risk. Most organizations are taking a piecemeal approach to zero trust. While this helps manage costs and resources, it can also introduce security vulnerabilities, especially when migrating from legacy architectures.
● Administrative cost constraints
The cost of migrating to ZTA can be high, especially if you are transitioning from a legacy system. A comprehensive zero trust framework may require building infrastructure from scratch. This is a long-term, multi-stage process that requires significant resources and time. While these costs can be controlled to some extent through incremental adoption, the speed and scale of adoption can be a challenge. Not to mention the cost of training talent and devoting resources to maintaining a Zero Trust architecture after implementation.
Even after a project is developed, companies need to set aside resources for ongoing maintenance. For example, micro-partitioning requires regular updates to IP data and configuration and verification of changes to minimize user access. Additionally, when administrators introduce new systems and applications to the network when required, they must add these systems and applications in a manner that is compliant with Zero Trust protocols, requiring additional framework development.
● Balance security and performance
Zero Trust puts security first by locking down access until the user is authenticated. The challenge is to ensure that zero-trust access management does not impact workflow and performance. For example, if an employee changes roles, they need to update access to the required data. If this role change is not recognized quickly, users will be locked out of access to critical files they need to do their jobs, impacting productivity and creating obstacles to workflow.
● Decision factors
Establishing a zero trust model in a large enterprise requires buy-in from key stakeholders to ensure proper planning, training, and implementation. The project involves nearly everyone in the organization, so managers and leaders must all agree on a plan. Because many organizations are slow to implement such changes, the decision factors alone can put a lot of pressure on successful project implementation.
06. How to implement zero trust
Modern access management starts with one question: Who has access to what?
Implementing Zero Trust doesn’t happen overnight. Typically, existing infrastructure can be integrated into a Zero Trust approach, but to reach maturity, most networks will need to adopt and integrate more capabilities and processes.
In fact, adopting a Zero Trust security posture incrementally can reduce risk, and from initial planning to basic, intermediate and advanced stages, the Zero Trust maturity model can gradually improve network security protection, response and operations.
Migrating to Zero Trust requires a complete understanding of the current state of the network architecture, including all of its assets (both physical and virtual), entities, and business processes. If this information is incomplete, a business's cybersecurity will have blind spots. By conducting a comprehensive audit and analysis of the current state of your network, you can plan what steps you need to take to optimize your network to achieve the ideal zero trust.
The National Institute of Standards and Technology (NIST) outlines six steps for moving to a zero-trust architecture.
● Identify actors in the enterprise
Who are your subjects and users? For zero trust to work, you need to know who your business principals are and what their access rights are. Note that users with special permissions, such as developers or system administrators, generally have blank access to legacy systems. Zero Trust should allow sufficient flexibility for these users while applying logging and auditing operations to verify and confirm access.
● Identify the assets owned by the business
A zero-trust architecture also requires the ability to identify and manage assets and devices. These assets include hardware components such as laptops, mobile phones, and IoT devices, as well as digital artifacts such as user accounts and applications. Managing enterprise assets involves not only cataloging, but also configuration management and monitoring.
● Identify key processes and assess risks associated with their execution
The next step is to inventory and sort the business processes and data. Business processes should inform how resource access requests are approved and denied.
● Develop policies for candidate ZTAs
The target service or process for the initial ZTA migration depends on several factors, including:
● Importance of processes to the organization
● Affected target groups
● The current status of the resources used by the workflow
Assess the value of assets and workflows based on risk. Consider all upstream resources, downstream resources, and entities that the workflow uses or affects. These all influence which assets are selected as candidates for migration.
● Identify candidate solutions
Once you have identified your potential shortlist, create and consider a list of solutions for implementing a zero trust strategy. When deciding which candidates are best for migration, keep the various Zero Trust principles and requirements in mind.
● Initial deployment and monitoring
Once you have selected your candidate workflows and determined which ZTA solutions you want to apply, you can begin deployment. This will be an iterative process that requires observing and monitoring new solutions, updating workflows as needed.
07. Best practices for zero trust
● Strict enforcement of authentication and authorization
All resources must be verified and authenticated. This often includes using technologies such as multi-factor authentication (MFA) to grant access rather than operating based on implicit trust.
● Maintain data integrity
Measure and monitor the security of all owned assets to ensure data integrity and reduce cyber threats.
● Collect data to improve security
Regularly collect data from multiple sources, such as network infrastructure and communications, to continually adjust and improve your security posture.
● Treat every data source and computing device as a resource
Any device that can access the network should be considered a resource. Keep all communications secure regardless of network location - location no longer means trust. Users and devices connecting through external or internal networks must meet the same security requirements to gain access.
● Grant resource access on a per-session basis
Enforce least privilege, requiring users to request access for each session.
● Use dynamic policies to moderate access
Protect resources with transparent, dynamic security policies that adapt to the changing needs of the network and its users.
Original link: https://www.strongdm.com/zero-trust
08. NOVA Technology-Zero Trust Solution
NOVA Technology's zero-trust solution uses identity to drive network behavior, dynamic verification, and continuous protection. It conducts all-round and ubiquitous security control on clients and realizes network security protection for computers, mobile phones, and other terminals. It has powerful capabilities. Compatibility and easy installation. Help enterprises build an end-to-end secure access system, improve business access efficiency, and respond to office security risks. Work with peace of mind anytime, anywhere, security is everywhere.
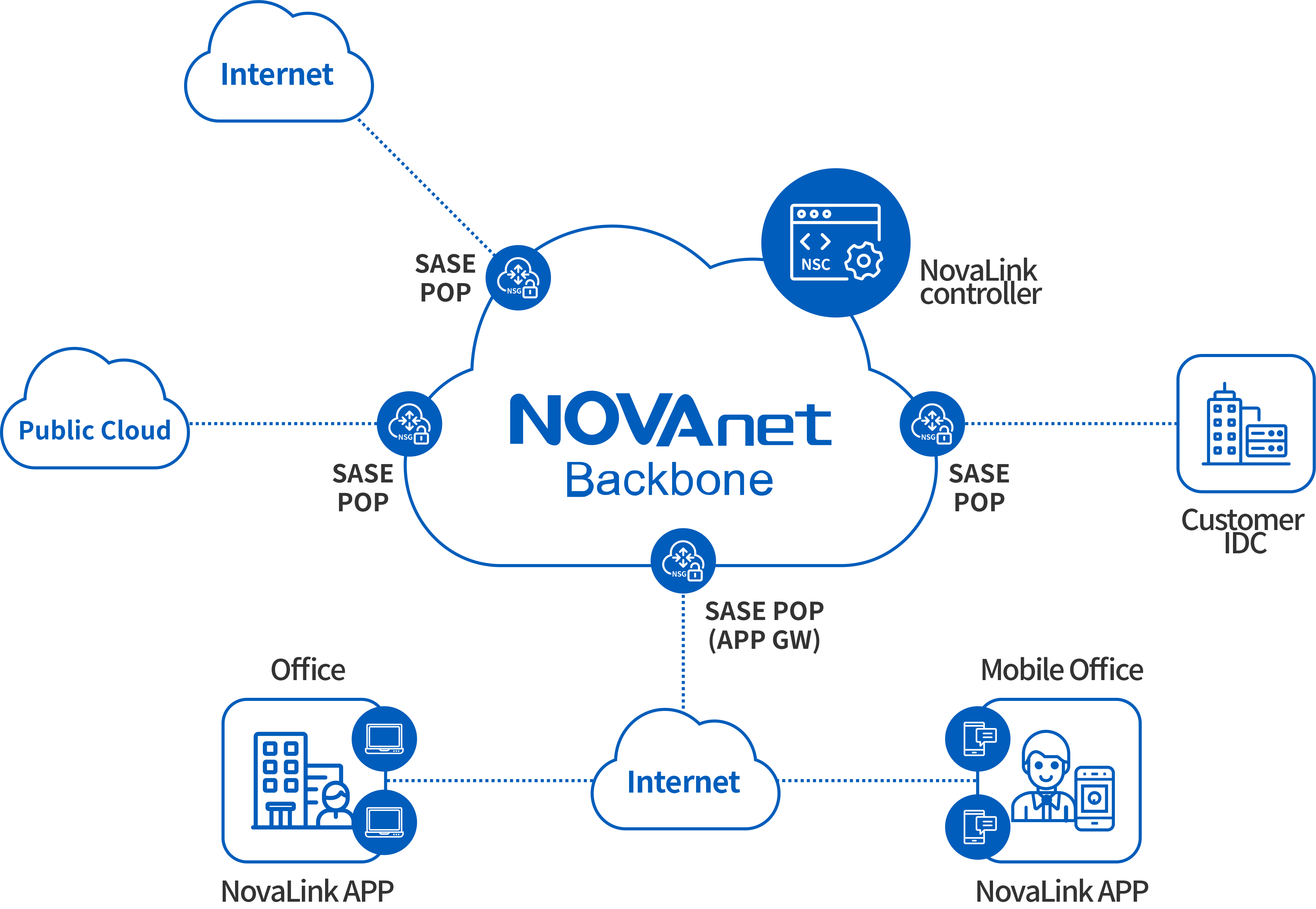
Solution value
● Continuous dynamic verification
Secure access based on the zero-trust principle can continuously and dynamically detect access behaviors, greatly reducing the security challenges faced by enterprises in application access and data transmission.
● Unified security strategy
From identity authorization to terminal management, security protection, early warning and traceability, the end-to-end closed-loop security access system strengthens the overall security status.
● Best user experience
Efficient and easy to use, one-click VPN connection; intelligent and easy management, self-service network diagnosis; compliance and security, terminal security baseline access.
At present, NOVA Technology's zero-trust terminal - NOVACLOUD NovaLink APP has been launched. It combines NOVA Technology's backbone network resources and operation services to provide customers with an integrated "cloud network security" SASE solution.








